Technical Surveillance Countermeasures Procedures
MICROSEARCH utilizes the latest industry standard and government level TSCM equipment. Our surveys include tests for devices such as:
|
The equipment seen listed in most “spy shop” catalogs does not fall into either of the preceding categories. The purpose of the TSCM survey is to locate any electronic intelligence gathering devices, and to identify any naturally occurring audio paths which could be exploited for espionage purposes. The survey will also identify procedural deficiencies which detract from the overall security of the facility or residence.
common elements of any tscm survey
|
Threat Appraisal and Plan Development
Every TSCM survey is different and there is no formula for developing the plan. Each situation must be evaluated based on the type of premises, possible adversaries, and additional circumstances discovered during the initial interview.
Non-Alerting Entry
MICROSEARCH investigators initially work in a non-alerting manner. In other words, if someone is listening, they will not be able to deduce what is being done. Investigators never discuss what they are doing while in a target room. If they need to ask questions or give directions, they leave the target room. The non-alerting entry includes a cursory search for active cameras and eavesdropping transmitters.
RF Spectrum Analysis
Several tests are conducted to locate various kinds of clandestine transmitters during this phase of a survey. The radio frequency spectrum is analyzed from 50 kHz to 21 GHz using a spectrum analyzer. All radio transmissions are both viewed and listened to as they are encountered with the spectrum analyzer or Omni Spectral Correlator (OSCOR). Any video signals occurring on frequencies other than those designated for commercial and public broadcast are viewed and identified. A computer-controlled communications receiver and a handheld radio frequency energy detector are used in conjunction with the spectrum analyzer. Spectrum analysis is frequently conducted during normal business hours from a location outside the facility.
Power lines and all other wiring are tested for the presence of carrier current transmitters. These are very low frequency (10 kHz to 700 kHz) transmissions with most of the radio frequency energy remaining within the wiring. An example of a carrier current transmitter is an FM wireless intercom system. All telephone lines in the target rooms are tested for the presence of carrier current transmitters.
Target rooms are inspected for the presence of infrared light using a viewer specifically designed to detect the type of light used by infrared eavesdropping transmitters.
Facilities using local area networks (LAN) are vulnerable to attack through a wireless access point on the LAN. This could be from an unencrypted LAN, or an unauthorized “rouge” access point. A personal computer equipped with software for network analysis is used to check for unauthorized wireless access points.
Power lines and all other wiring are tested for the presence of carrier current transmitters. These are very low frequency (10 kHz to 700 kHz) transmissions with most of the radio frequency energy remaining within the wiring. An example of a carrier current transmitter is an FM wireless intercom system. All telephone lines in the target rooms are tested for the presence of carrier current transmitters.
Target rooms are inspected for the presence of infrared light using a viewer specifically designed to detect the type of light used by infrared eavesdropping transmitters.
Facilities using local area networks (LAN) are vulnerable to attack through a wireless access point on the LAN. This could be from an unencrypted LAN, or an unauthorized “rouge” access point. A personal computer equipped with software for network analysis is used to check for unauthorized wireless access points.
Telephone Instrument and System Analysis
During this phase of the survey the telephone instruments, facsimile machines, speaker phones, wiring, and telephone system are examined for the presence of listening devices. Depending on the type of telephones and/or system, they will be tested using, TALAN digital phone analyzer. Telephone instruments are subjected to fluoroscopic (x-ray) survey in an attempt to locate eavesdropping modifications. When the instruments are found to be free of modifications they are sealed with a tamper-evident tag to protect against future attempts at modification. In some cases the lines are physically checked from the phone instrument to the telephone terminal closet. This is done by injecting an electronic tone into the line, then tracing its path using a special receiver that detects the tone. Any branching of wires will be detected in this way.
The telephone terminal equipment and wiring is inspected for modifications and extra equipment that does not belong there. The radio frequency spectrum is analyzed while each telephone instrument handset is alternately lifted and replaced. This procedure will activate any eavesdropping transmitter attached to the telecommunications equipment.
The telephone terminal equipment and wiring is inspected for modifications and extra equipment that does not belong there. The radio frequency spectrum is analyzed while each telephone instrument handset is alternately lifted and replaced. This procedure will activate any eavesdropping transmitter attached to the telecommunications equipment.
Physical Search
During this phase of the survey each target area is examined for several types of threat. Investigators will look for hidden microphones, suspicious wiring, concealed radio transmitters, modified communications or power equipment, and susceptibility to laser microphones. An ORION Nonlinear junction detector (NJD) is used to check walls, ceilings, furniture, etc. for the presence of electronic devices. This includes "bugs" that have been switched off by remote control or are no longer operating because the batteries have gone dead. A high intensity ultraviolet survey light is often used in conjunction with the NJD to locate evidence of tampering to walls and other painted surfaces. A metal detector and densimeter are frequently used during the physical survey. Many objects, such as picture frames, objects d’ art, and lamp bases are x-rayed. This is particularly true if the object produced an alarm from the NJD.
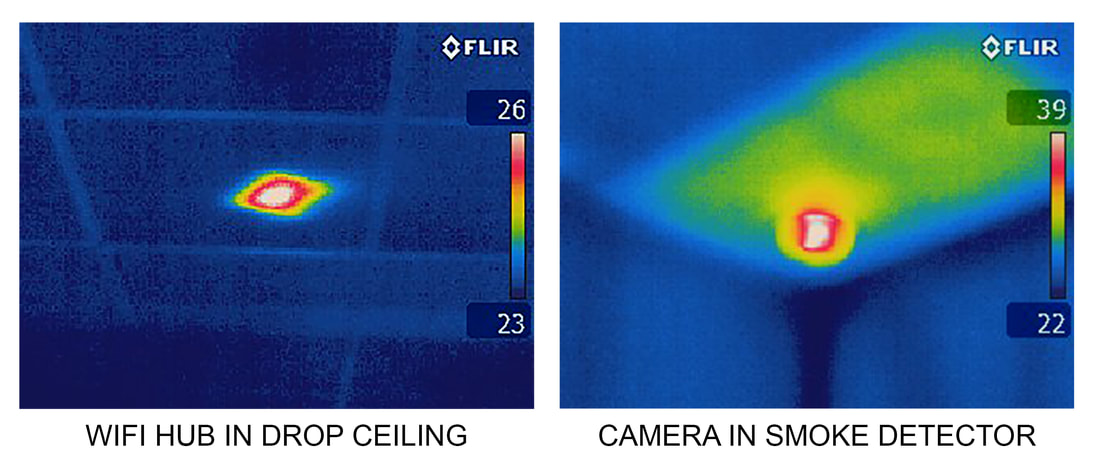
A thermal imaging camera is used to scan the target rooms from floor to ceiling. The thermal camera detects variations in temperature, making anything generating heat visible. The thermal camera is sensitive enough to detect the temperature difference caused by a human hand touching a tabletop for less than one second.
Metal water pipes and conduit which pass through target rooms or areas are checked to determine if they are conducting audio. This is done by connecting a contact microphone and audio amplifier to the pipe or conduit and listening for audio from the target room or area. This is a particularly important test if the facility under survey has a SCIF (Sensitive Compartmented Information Facility) room requirement.
The TSCM manager also identifies any areas where direct listening is possible. This is known as the audio conduction test, where a sound source is placed in a target room, then listened for in adjacent rooms or areas.
A thermal imaging camera is used to scan the target rooms from floor to ceiling. The thermal camera detects variations in temperature, making anything generating heat visible. The thermal camera is sensitive enough to detect the temperature difference caused by a human hand touching a tabletop for less than one second.
Metal water pipes and conduit which pass through target rooms or areas are checked to determine if they are conducting audio. This is done by connecting a contact microphone and audio amplifier to the pipe or conduit and listening for audio from the target room or area. This is a particularly important test if the facility under survey has a SCIF (Sensitive Compartmented Information Facility) room requirement.
The TSCM manager also identifies any areas where direct listening is possible. This is known as the audio conduction test, where a sound source is placed in a target room, then listened for in adjacent rooms or areas.
Findings and Recommendations
|
An oral report is given at the conclusion of the survey. A detailed written report is delivered to the location of your choice via email or Federal Express within five business days. The comprehensive report is proof of your due diligence and helps satisfy your requirement to protect proprietary data as described in the Economic Espionage Act of 1996. The report includes objective and reasonable recommendations to improve security and serves as an independent security audit.
If a hostile eavesdropping device is discovered there is an obligation to notify law enforcement. It is our recommendation that the notification be made to the Federal Bureau of Investigation. Failure to notify proper authorities that a felony has been committed is itself a felony under United States Code Title 18, Part I, Chapter 1, Section 4. |